Trusted Edge
ADI Assure™ is a suite of products that provides robust protection against security threats to deliver a persistent state of assurance. With our trusted edge solutions, your security boundary is closer to the data’s origin, resulting in higher confidence in its authenticity and trustworthiness. We are committed to helping our customers more rapidly deploy connected, smart solutions that elevate their impact in the world.
Value and Benefits
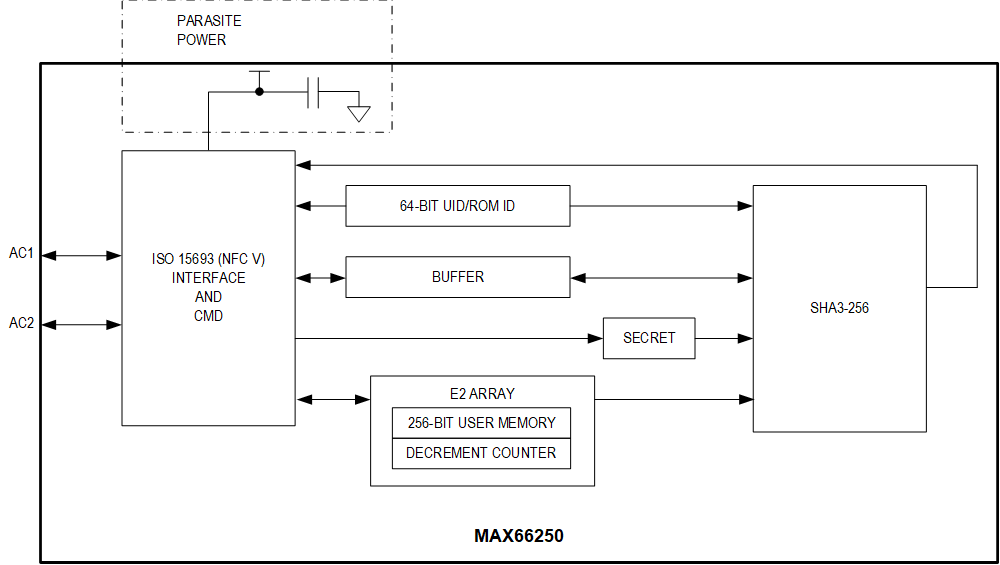
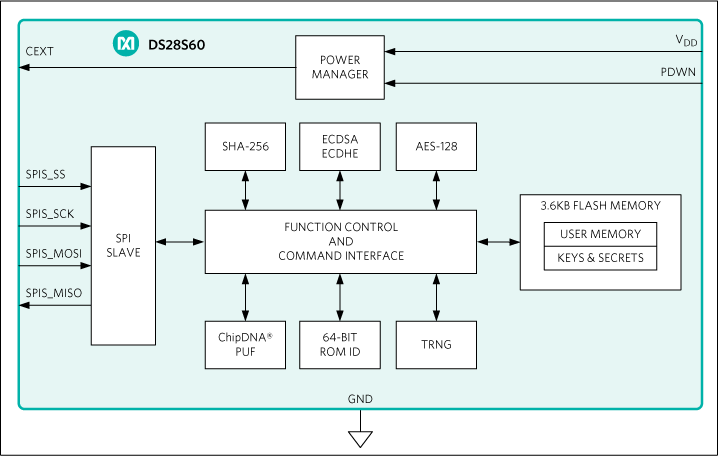
We built a trusted foundation to help our customers meet industry cybersecurity standards and regulatory requirements swiftly and bolster their defenses against evolving security threats throughout the life of their products. Our leading-edge technologies such as ChipDNA® PUF, tamper-resistant key storage, and advanced crypto algorithms enhance security architectures and provide heightened resistance against invasive and non-invasive attacks. Our rich portfolio of scalable and flexible security solutions with hardware-based Root of Trust and software services offers sustained protection and ease of integration, ultimately safeguarding systems, accelerating the cybersecurity certification journey, and enabling resilience for the long term.


Preserves customer time to market through secure design standards and compliant security solutions


Provides trust assurance with embedded security and secure lifecycle management


Elevates security posture through innovation where analog meets digital
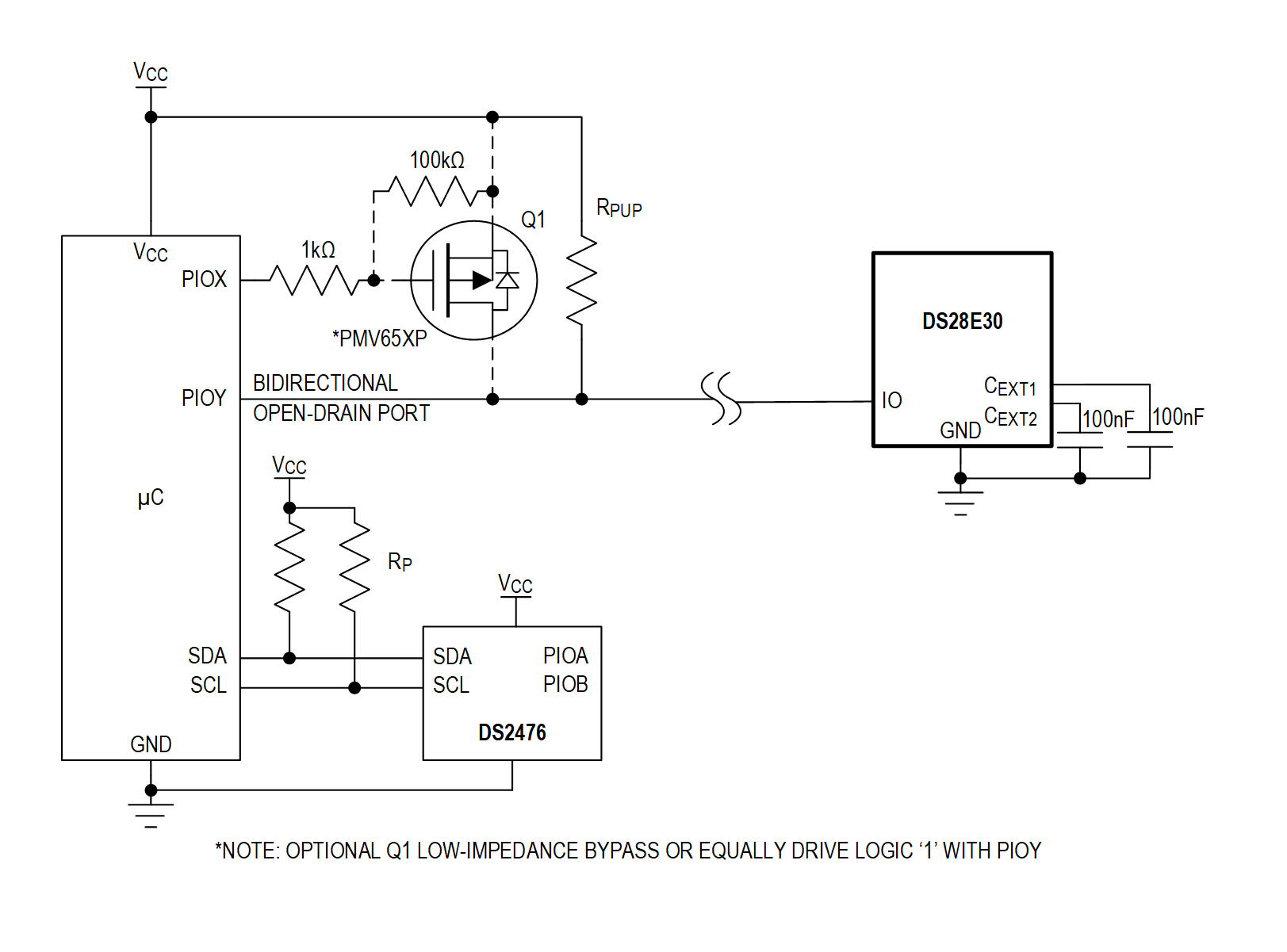
Learn how ADI’s extensive portfolio of turnkey secure authentication products with hardware root of trust and secure key management deliver a complete solution package to strengthen industrial control system security architectures.

Trusted Edge Security Architecture
Accelerating innovation at the edge means enabling our customers to focus on what they do best. Our Trusted Edge Security Architecture allows you to scale edge applications across a single security API, while giving you a flexible approach to hardware platforms and security assurance levels.

Industrial Cybersecurity Demystified
Digital transformation has been a catalyst for change in industry, with the production of more and more data to enable real-time decision-making for increased automation and enhanced process efficiency. This eBook explores the industrial cybersecurity related trends, challenges and solutions to make industrial automated control system resilient to cyberattack.
Read the eBook
| English | German | French | Italian |
Solution Resources
Interactive Signal Chains


Training and Support
Trainings and Tutorials
{{modalTitle}}
{{modalDescription}}
{{dropdownTitle}}
- {{defaultSelectedText}} {{#each projectNames}}
- {{name}} {{/each}} {{#if newProjectText}}
-
{{newProjectText}}
{{/if}}
{{newProjectTitle}}
{{projectNameErrorText}}