Lockbox Secure Technology
Lockbox™ Secure Technology for Analog Devices Blackfin Processors is based upon the concept of authentication of digital signatures using standards-based algorithms and provides a secure processing environment in which to execute code and protect assets. Lockbox Secure Technology is comprised of a combination of hardware and software mechanisms that provide the means for developers to implement security measures that range from safeguarding secrets such as OEMs' intellectual property, to verifying the identity of devices and users for protected e-commerce and social networking, to digital rights management (DRM) content protection.
More specifically, Lockbox Secure Technology provides one-time programmable (OTP) memory and a secure processing mode (Blackfin Secure Mode) to enable these capabilities. Its public, non-secure, user-programmable area of OTP memory is suited for storing public keys to authenticate the system in a manner that is controllable and configurable by the developer. A private, secure, user-programmable area of OTP memory lets developers program their own private device assets such as private keys, and maintain the confidentiality and integrity of those assets. Furthermore, using Secure Mode on Blackfin allows systems to be implemented in which only authenticated, trusted code is allowed to execute on the processor within a secure processing environment.
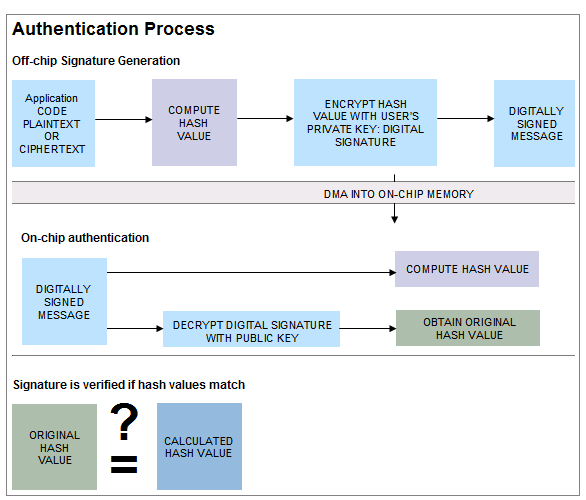
| The diagram shown above represents a simplification of the digital signature creation and verification process implemented in Lockbox. |
ECDSA Signature Verification Process
Lockbox Secure Technology uses standards-based cryptographic algorithms. Digital Signature Authentication on ADSP-BF54x and ADSP-BF52x utilizes the following:
- Elliptic Curve Cryptography (ECC) asymmetric cipher1
- SHA-1 Secure One-Way HASH2 2
-
ECDSA Signature Verification, a subset of ECDSA, is implemented in the ADSP-BF54x and ADSP-BF52x
products. 3
Benefits
Authenticity/Origin Verification
- Blackfin Lockbox™ Secure Technology allows for verification of a code image against its embedded digital signature, and provides for a process to identify entities and data origins.
Integrity
- Developers can use a digital signature authentication process to ensure that the message or the content of the storage media has not been altered in any way. Integrity can be verified using Lockbox's authentication of digital signatures.
Confidentiality
- Cryptographic encryption/decryption supports situations that require the ability to prevent unauthorized users from seeing and using designated files and streams. Lockbox's secure processing environment (Secure Mode) and secure memory support confidentiality.
Renewability
- Renewability refers to the updating of system components to enhance security.
- Lockbox's Unique Chip ID enables end users to identify each Blackfin processor and hence each OEM device in which the processor resides.
- This Lockbox feature can be used in support of revocation and renewability of licenses in case of security violations in Digital Rights Management systems.
- Unique Chip ID can also be utilized to "bind" processor to one specific boot source/device. Facilitates anti-theft schemes and prevents OEM device cloning.
Additional Reading
Product Information
1 These implementations are based on the Elliptic Curve Digital Signature Algorithm (ECDSA) specified in FIPS 186-2 with Change Notice 1 dated October 5, 2001, Digital Signature Standard (DSS), and specified in ANSI X9.62-1998.
2 SHA-1 is based on the publicly available standard for FIPS 180-2 (Secure Hash Signature Standard (SHS) (FIPS PUB 180-2).
3 ECDSA implementation on these Blackfin products only supports the Koblitz curve.